IT Managed Services is our life.
We sell one service, an abundance of helping experience
Our Core Focus
-
Complete outsource IT service provider
-
24/7 support staff with alerting and escalation
-
Future Focused, 100% Decentralized and Distributed
Our goal is to help as many people as we can everyday using the five-brains framework for IT management. We work to move small and medium business up the IT maturity model by implementing standardized components, planned maintenance and best practices.
We focus on responsiveness and throughput with a personal touch. We have extensive experience in support, networking, security, data center, backup & disaster recovery, strategy and architecture. We practice promise based management and leverage deep entrepreneurial experience. We work to deliver an abundance of helping experiences and uncommon knowledge.
How does all of this work?

Managed Services IT Operations Maturity Model
Our IT managed service delivery model moves your business from left to right up the IT maturity stack (above). Our business is purpose built to scale your IT business components to produce reliability and IT maturity. We make recommendations about the future and work through them together.
Our Uncommon Skills
-
Experts in Hybrid Cloud computing environments
-
Data Center designs, building, hosting, and ongoing management
-
Complex networking architecture, troubleshooting, redundancy, high availability
-
Agent-less and Agent-based monitoring technologies
-
Security Assessments and Managed Security solutions
-
Telephony (PBX) systems, on-prem, or in-cloud
-
Wholesale software licensing on industry leading MSP tools
-
Infrastructure cabling diagnostics and certification
-
Forensic data acquisition, recovery, and analysis
-
Healthcare Information Systems Compliance and Validation
-
Cloud backup and hardware-based disaster recovery solutions
-
Master Agency for Telecommunications and Bandwidth
-
Wireless Networking Assessments and Heat mapping
-
Emerging Technology Consulting: AI, IoT, Blockchain
How Do We Incorporate IT Security?
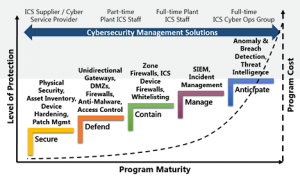
IT Security Operations Maturity Model
We layer IT Security on top of IT Maturity. The IT Security landscape has been gradually growing in size and complexity. Many different hardware and software solutions exist that work to create layers of security. Different layers have different attack surfaces that need a unique formula of IT analysis and review. At each layer we work to log events that transform into dashboards and feed systems that help us narrow in on key information. This key info triggers additional review and a bounty. All this is made possible by adopting and following the IT maturity models(s) and aligning with a trusted expert in the IT marketplace.
How Do We Scale The Process?
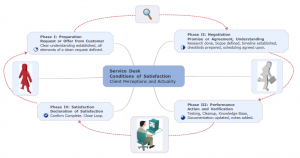
Closed Loop Customer Workflow
